Cloudflare Under Attack Mode
Cloudflare gives a complete degree of protection from a broad scope of attacks. We do this while limiting bogus positives or inconveniences to genuine clients. Cloudflare didn’t start as a DDoS alleviation administration, yet we’ve quickly discovered that cloudflare under attack mode are acceptable at protecting locales from these attacks. Today we’re offering another protection mode to make our DDoS protection stunningly better.
A Brief History of DDoS
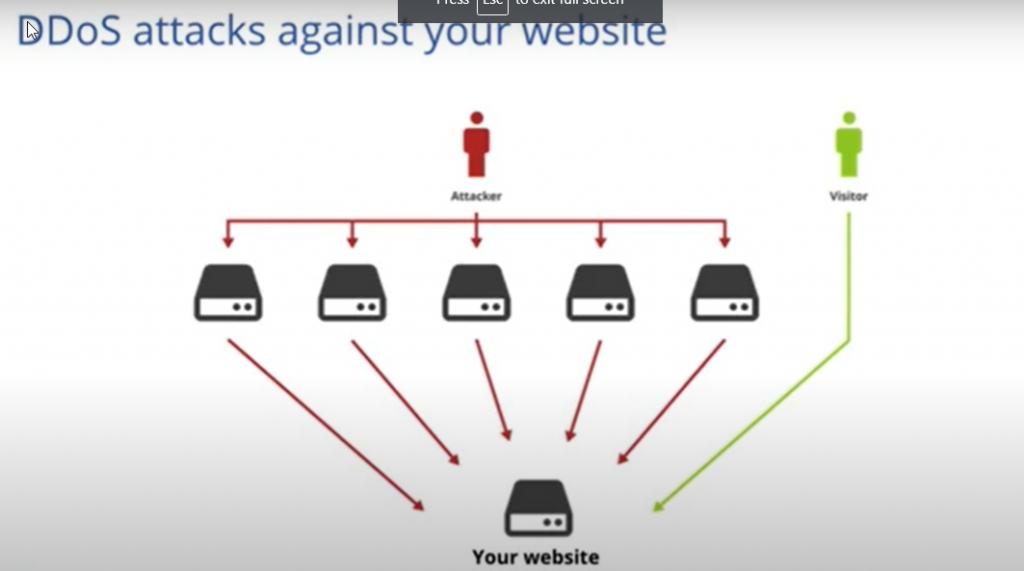
In the OSI model, customary DDoS attacks focused on Layer 4. The supposed “transport” layer of the organization stack determines the convention (e.g., TCP or UDP). These attacks flood an interface with trash traffic to overpower it’s assets somehow. Generally, the assault tops off the limit of an organization switch or overcomes a worker’s organization card or CPU’s capacity to deal with the traffic.
Cloudflare has generally moderated these attacks by working out noteworthy limit over our organization. We have fat lines and loads of machines to retain surges of traffic. We likewise utilize the Anycast convention, which impacts dispersing the heap of a circulated assault over different server farms, diminishing the introduction of the single expected purpose of disappointment. The outcome is that no bundles from a customary Layer 4 assault will arrive at a site behind Cloudflare.
HTTP-Based Attacks
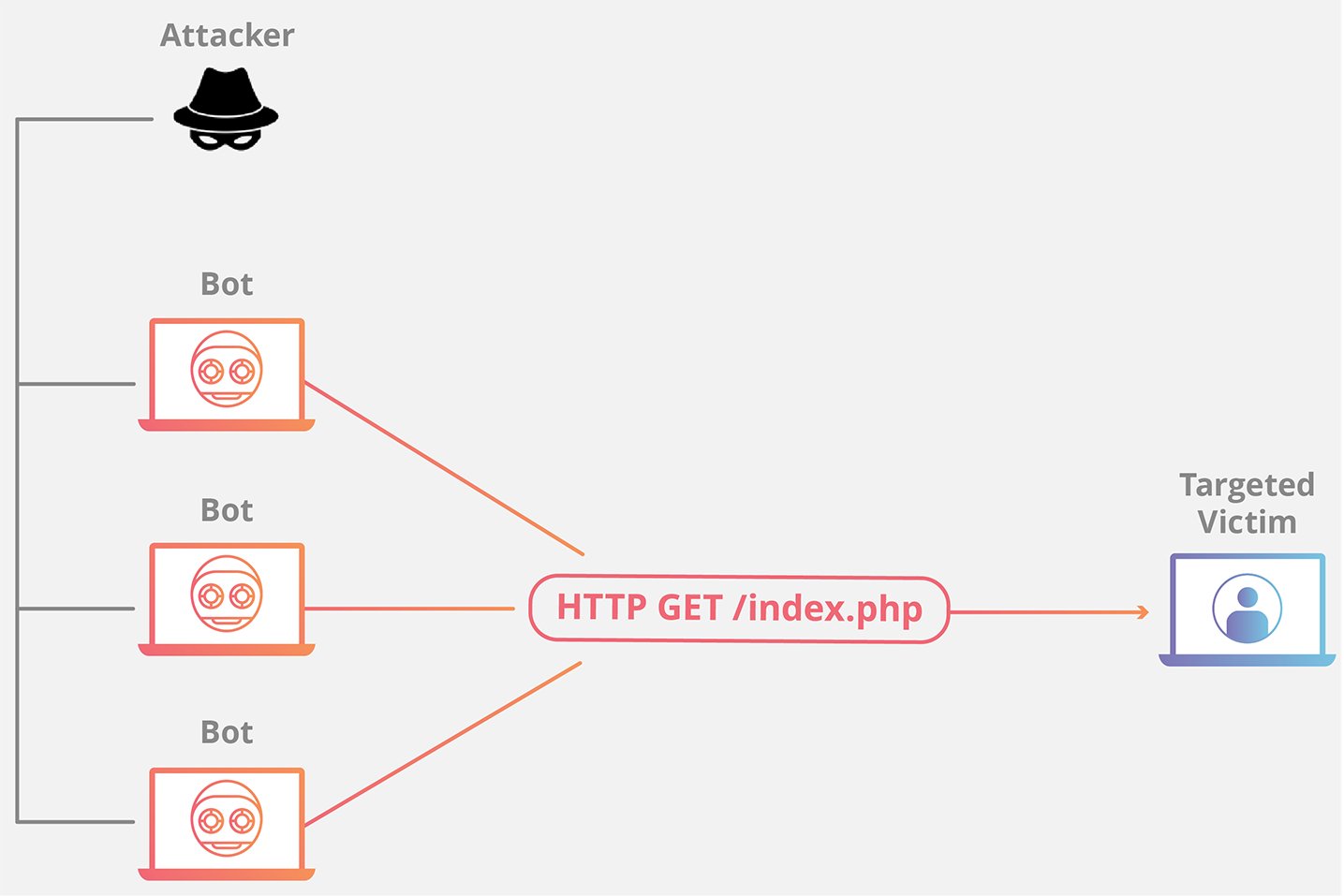
Another variety of attacks targets Layer 7, the “application” layer. These attacks center around explicit attributes of web applications that current bottlenecks. For instance, the alleged Slow Read assault sends bundles gradually over various associations. Since Apache opens another string for every association, and since associations are kept up as long as there will be some traffic being sent, you can overpower a web worker by exhaust its string pool generally without any problem.
Cloudflare has insurances set up against many of these attacks, and in genuine encounters, we by and large decrease the HTTP assault traffic by about 90%. For most episodes and the majority of our clients, this has been sufficient to keep them on the web. Nonetheless, 10% of traffic that gets past our conventional securities can, at present, be overpowering to either clients with restricted assets or despite massive attacks. We needed to help in these cases as well, so today we’re reporting something new.
I’m Under Attack Mode
Presenting “I’m Under Attack Mode.” The name is entirely plain as day: it’s another protection level you can set for your site when you’re enduring an onslaught. The impact is that we will include a different arrangement of insurances to stop possibly noxious HTTP traffic from being passed to your worker. While we play out some of the extra checks, the main thing recognizable to real guests to your site is that they’ll see an interstitial page for around 5 seconds while inspections are finished when they initially show up. Consider it a test where the tests are programmed, and guests never need to fill in a CAPTCHA.
After confirmed as authentic by the computerized tests, guests can peruse your site unrestricted and won’t usually see the test page once more. Javascript and treats are required for the tests and recording the way that the tests were effectively passed. We’ve also planned the new checks to hinder web index crawlers, current allowlists, and other pre-verified traffic. Subsequently, empowering I’m Under Attack Mode won’t contrarily sway your SEO or known genuine guests. What’s additionally relaxed is that information on assault traffic that doesn’t pass the programmed registers is taken care of back with CloudFlare’s framework to improve our customary insurances.
While Cloudflare didn’t begin as a DDoS moderation administration, we have understood this is a region where we can give a ton of advantage and reasonably. I’m Under Attack Mode is the first of a few new highlights we’ll be delivering over the coming month to offer a full gauntlet of DDoS protection.